 Swipe / Scroll to Navigate
Swipe / Scroll to Navigate
I've been a professional ethical hacker since 2019. I have experience pentesting web applications, networks, thick clients, APIs, and other industry-specific systems in OT (Operation Technology) and IT (Information Technology) environments. I enjoy the complexity of the web and the pleasure of learning new technologies.
While I'm most experienced in ethical hacking, I have also worked on malware research, incident response, purple teaming, and software development. During my initial days in the corporate world, it was my conscious decision to work for different teams and understand their challenges. When you have worked in a development team, you know the best ways to help them as a pentester.
I completed my dual (Bachelor's + Master's) degree from IIT Madras with published research on malware evasion techniques. D-TIME is the malware obfuscation framework I developed during the study. The paper and the PoC were published in WOOT'19.
Cert-Fixer is a Magisk module that installs custom CA certificates to Android's system certificate store. To install system CA certificates using Cert-Fixer, you first install Cert-Fixer as a module in Magisk, install your custom CA certificates under the user certificate store, and reboot. Cert-Fixer will copy all your user CA certificates to the system certificate store during boot up. Cert-Fixer is tested against Android 14 and 15 (API 34 and 35). This article is a step-by-step guide for installing custom CA certificates on the system store of Android 15 (API 35).
This article describes my first bug bounty report. I was on holidays, and I was getting bored. So, I thought of doing a bit of bug bounty. Here is what I found!
D-TIME is a runtime obfuscation framework for malware in Windows. The framework was developed as a part of my Master's Project and published in WOOT'19. In addition to D-TIME, the paper also introduces SCBC, a robust covert broadcasting channel for Windows as well as Linux based operating systems.
There is very little documentation on the structure of SSH keys and certificates. Combining the information from various RFCs and the source code of OpenSSH, I have put together the format for SSH keys and certificates that are based on RSA.
Like most of my blog, this article was also written for my own reference, but might help you too! There are also links to parsers that you can use to parse SSH keys and certificates.
As a developer, how many times have you run unknown scripts (from the internet) in your system? Many times, the developers are limited by time or motivation to read through the scripts they find online. And sometimes, it's not even practical to go through every package and script that we run or install. What if one of those scripts you run contains malware? This is especially alarming since most of us use the same laptop in our developer and personal lives.
Two popular choices that can solve this issue are virtual machines and Docker containers. You can develop in a virtual machine or a docker container to isolate your developer life from your personal life. But virtual machines are resource-heavy and Docker containers might not be suitable for a long-term development plan. What you need is a container that is easy to manage and lightweight. And that's why you need LXC!
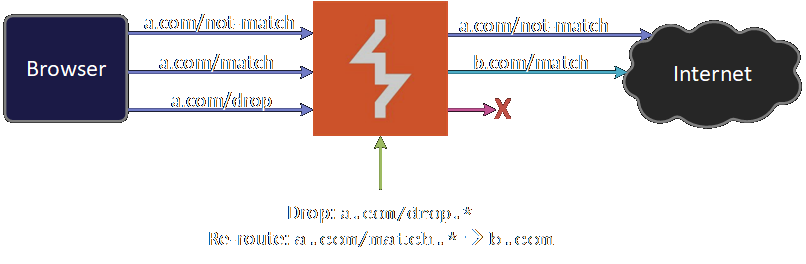
Burp Suite is one of the most popular tools used for web application pentesting. Advanced Proxy extension for Burp Suite helps you drop or change the destination of a request by regex matching.
SSH port forwarding is a mechanism in SSH for tunneling application ports from the client machine to the server machine, or vice versa. It can be used for adding encryption to legacy applications, going through firewalls, and some system administrators and IT professionals use it for opening backdoors into the internal network from their home machines. It can also be abused by hackers and malware to open access from the Internet to the internal network.
~ ssh.com
The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service, either on behalf of a resource owner by orchestrating an approval interaction between the resource owner and the HTTP service, or by allowing the third-party application to obtain access on its own behalf.
~ IETF
Docked-VPN is a Docker-based proxy with support for OpenVPN. It enables you to route only the applications of your choice through VPN. For example, you can add VPN to Firefox but not Chrome. With Docked-VPN, using VPN is as simple as connecting to a Proxy. Docked-VPN can be used with any software that supports a proxy.
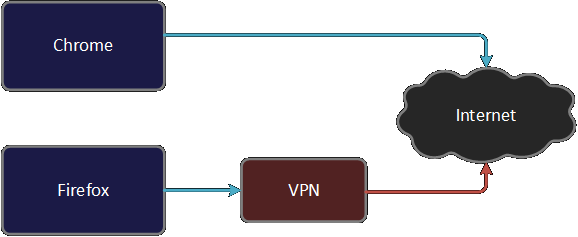
Sometimes, you might want to work on and off VPN simultaneously. For example, you might want to be able to visit websites restricted for your country by using a VPN. But at the same time, you might want to stay off-VPN for your regular browsing needs. This could be because you don't want to slow down your regular browsing or you want to keep your default location for this traffic. This article will explain how you can maintain the desired applications on and off VPN seamlessly.
While this article can be used for any application, we will take browsers as examples as browsing is the most common network activity.
Windows Challenge/Response (NTLM) is the authentication protocol used on networks that include systems running the Windows operating system and on stand-alone systems.
~ MSDN Docs
Socket programming is easy. Languages like Python provides robust libraries to create and manage sockets and socket communications. However, do you know the packet-level details of the socket library functions/commands that you execute? If you are curious about it, you came to the right place.
The best way to learn is to experiment. So in this article, we will set up a sender, listener and Wireshark to experiment and learn.
This post about the two-day “Ethical Hacking Workshop” I conducted as a part of Shaastra 2019.
Watching the glittering faces of each participant and their proud in each hack was an amazing experience! Here is a short summary of the workshop.
In a typical covert channel attack, we have two processes (a sender and a receiver) trying to communicate with each other though they are not allowed to do so by the security policies. While there are multiple cache-based attacks possible, most of them have extremely low bandwidth.
This article discusses a new variant of the cache-based covert channel attacks that promises a high bandwidth.
This article is a deep dive on CVE-2017-0358. The article starts with an introduction to the attack and then explains the basics of the components present in the attack and finally details the vulnerability and exploit implementation.
Disclaimer: This article is intended for educational purposes only.
This article analyses one of the HackerRank Questions and solves it using simple data structures.
Question: You are given a 2D matrix A (of dimension M×N) and a positive integer R. You have to rotate the matrix R times and print the resultant matrix. Rotation should be in the anti-clockwise direction.
It's obviously tiring when you have to download all videos of an NPTEL course. This project is aimed at making NPTEL video download effortless. The user just needs to provide the course ID, select the videos to download and sit back and relax.